In this article, we will walk the reader through configuring Auth0 as an Identity Provider (IdP) and SiteMinder as the Service Provider (SP).
Create Enterprise Connection in Auth0
Navigate to the Enterprise option under Connections in the Auth0 dashboard. Select Create (+) on SAML option.
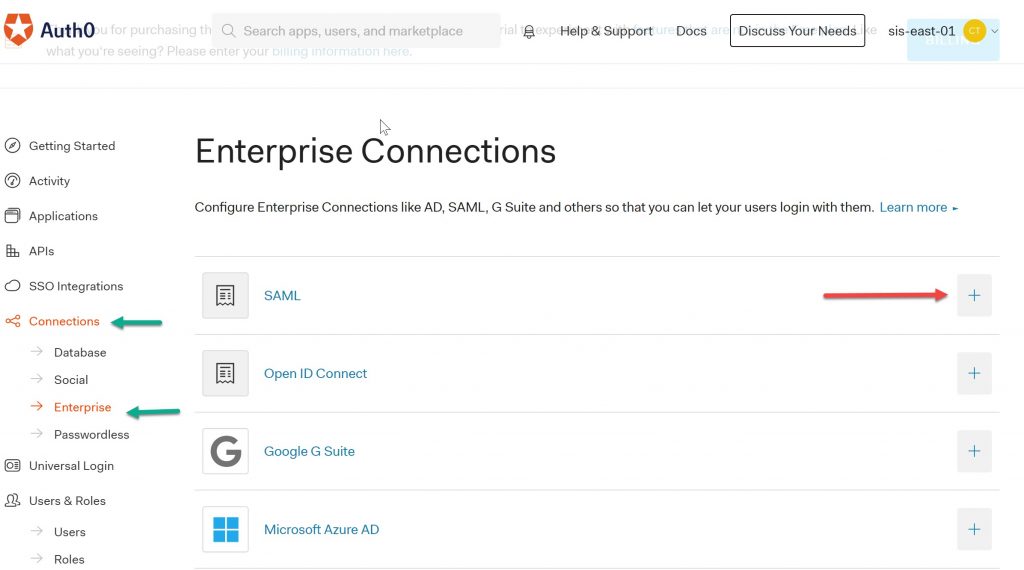
Select “Create Connection”.
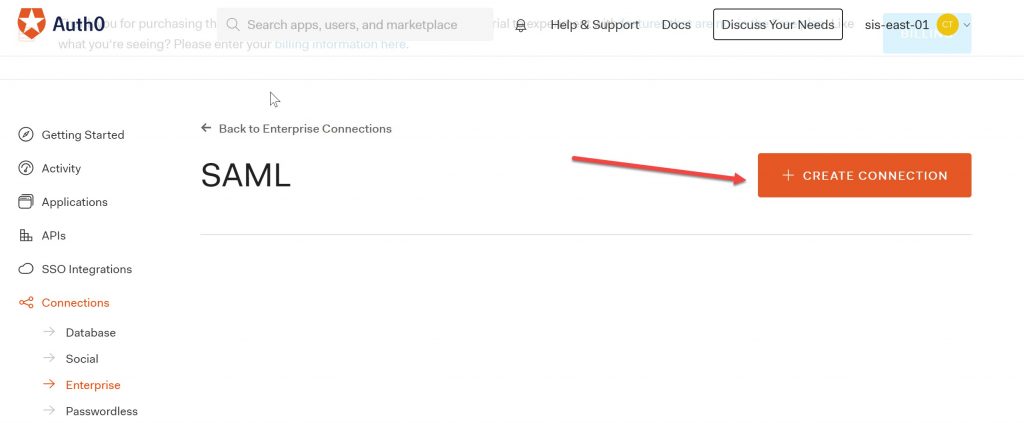
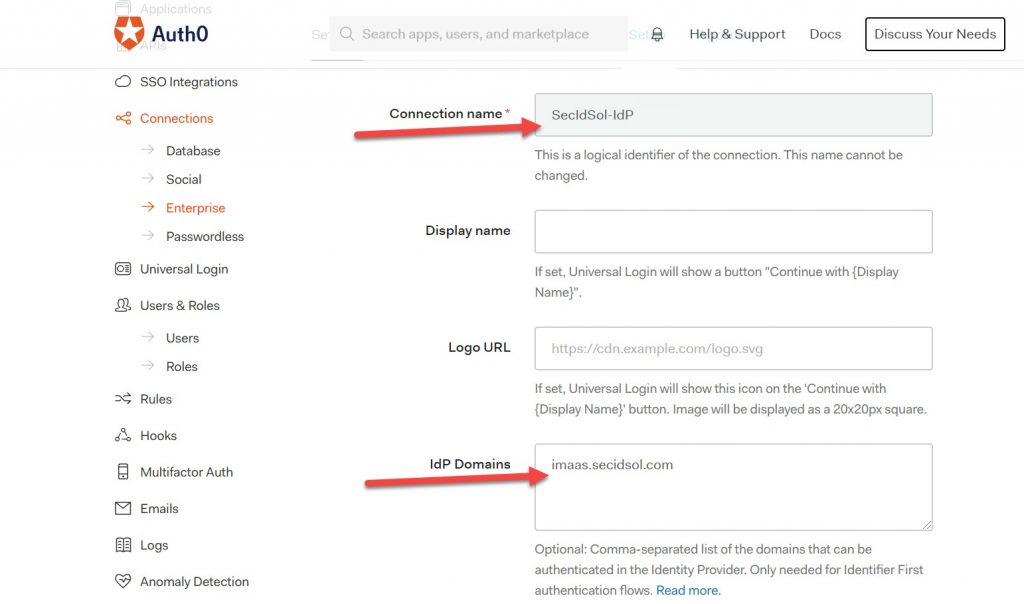
Name your connection and the IdP Domains.
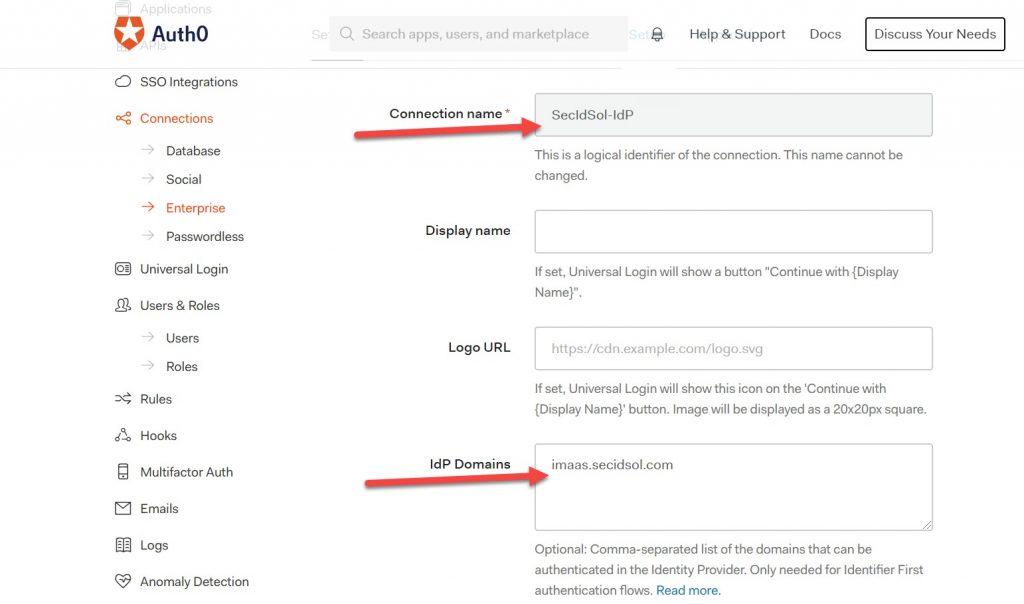
Enter the assertion consumer URL from SiteMinder as value for the login URL:
https://authservices-staging.imaas.secidsol.com/affwebservices/public/saml2assertionconsumer
Enter the SLO URL from SiteMinder as the value for the logout URL:
https://authservices-staging.imaas.secidsol.com/affwebservices/public/saml2slo
Ensure the Protocol Binding matches the SiteMinder SP. In this example, we are using HTTP-POST.
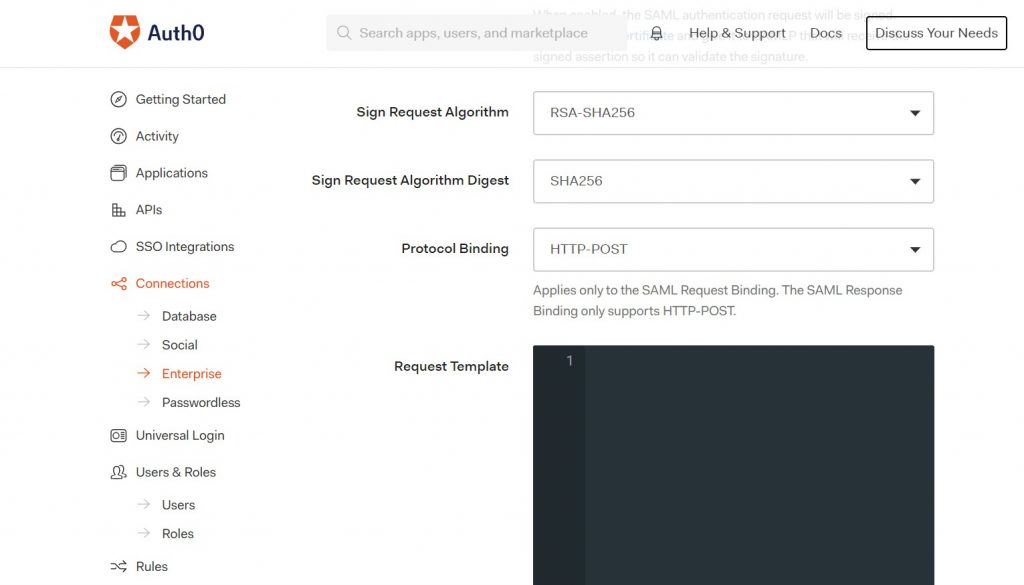
Create Application for the IdP
Auth0 will challenge the user for authentication based on the application they are attempting to access. An application must be created in Auth0 in order to bind the SAML flow.
In the Auth0 dashboard, go to the applications tab and create an application. For the this example, we selected “Regular Web Application”. The technology type selection that follows is not important for SAML authentication because the integration is with the SAML Service Provider, not the application.
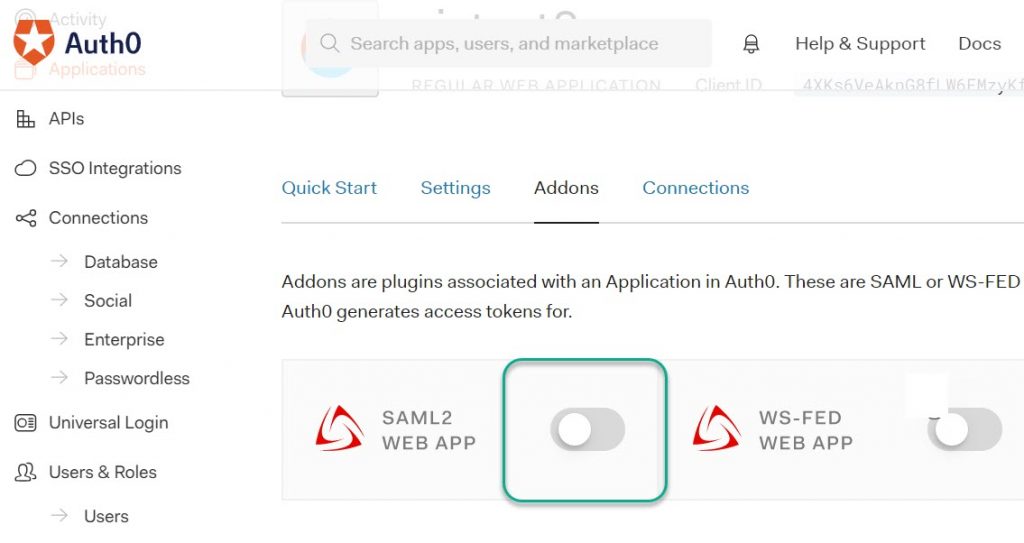
Select the Addons tab and select the ‘SAML2 Web App” option.
Enter the Application Callback URL (which is the same value as the assertion consumer url). Uncomment the audience line by removing the ‘//’ preceding the audience name/value pair. Enter the audience value in the quotes. (Note: We recommend setting the audience value to the SP ID.) Enable the SAML2 Web App add-on for the application to save the changes.
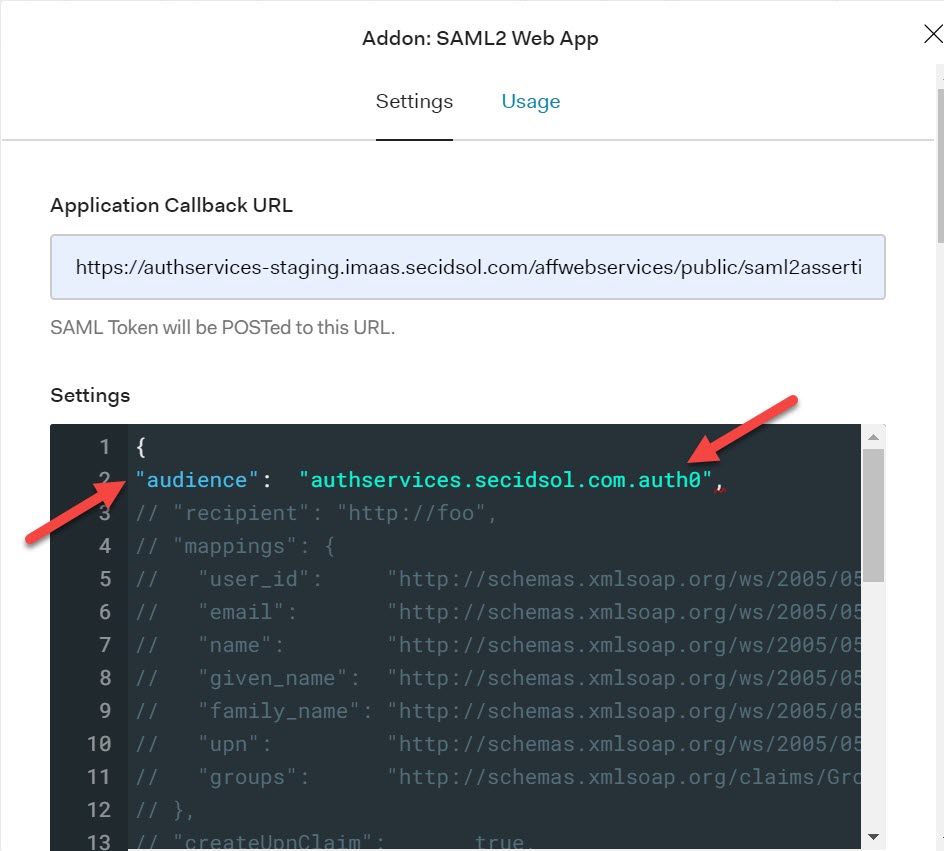
After saving the configuration and selecting the SAML2 Web App, the settings will resemble the following:
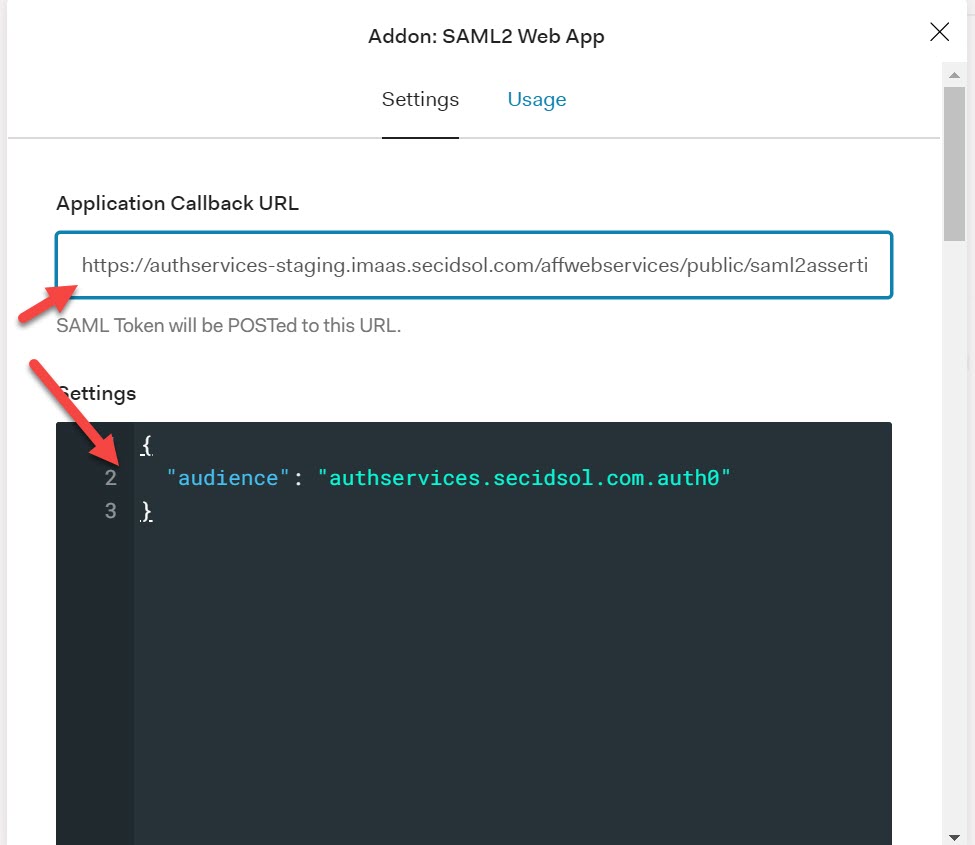
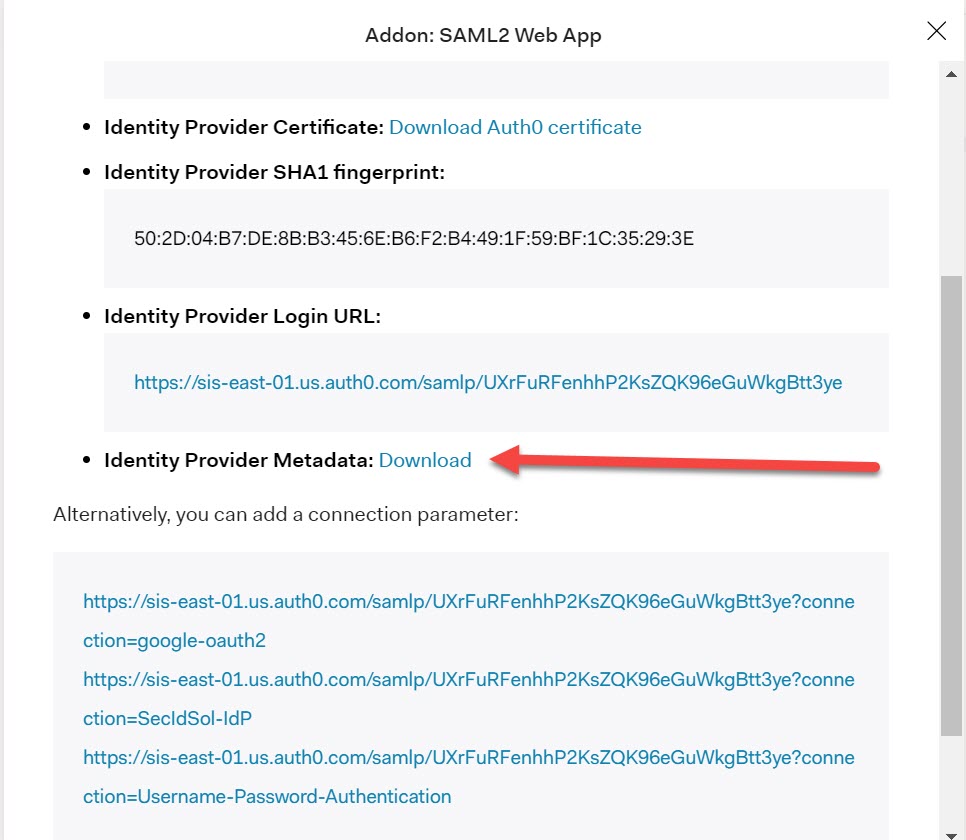
Select the Usage tab and click ‘Download’ for the Identity Provider Metadata.
SiteMinder Configuration
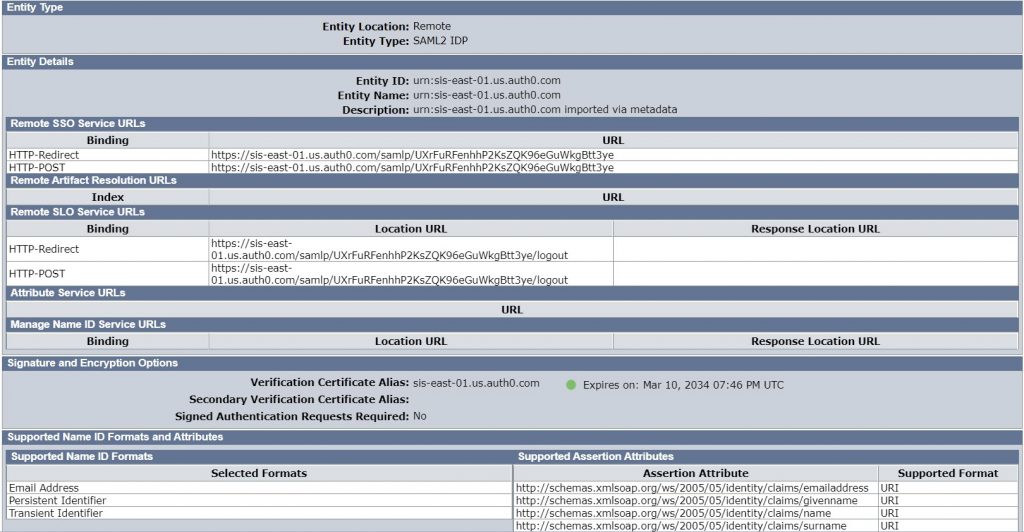
Create Entity
In the SiteMinder WAMUI, import the metadata via the entities option under Partnership Federation. After importing the entity, the screen will resemble the following:
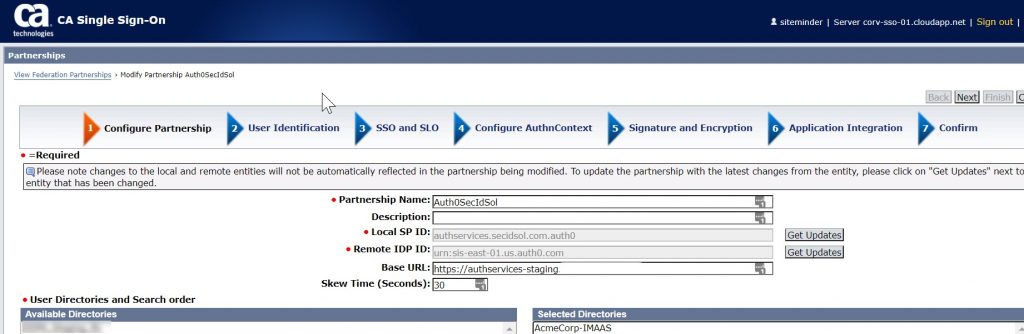
Create Partnership
Select the SP –> IDP option. Select the IdP that was imported in the previous section and the desired SP. Enter your Base URL value.
Enter the ldap search specification for your configuration. We have elected to store the Auth0 user_id as the GUID in our directory.

Keep in mind that Auth0 will use the value of user_id in the nameid of the assertion, which will look like the following:
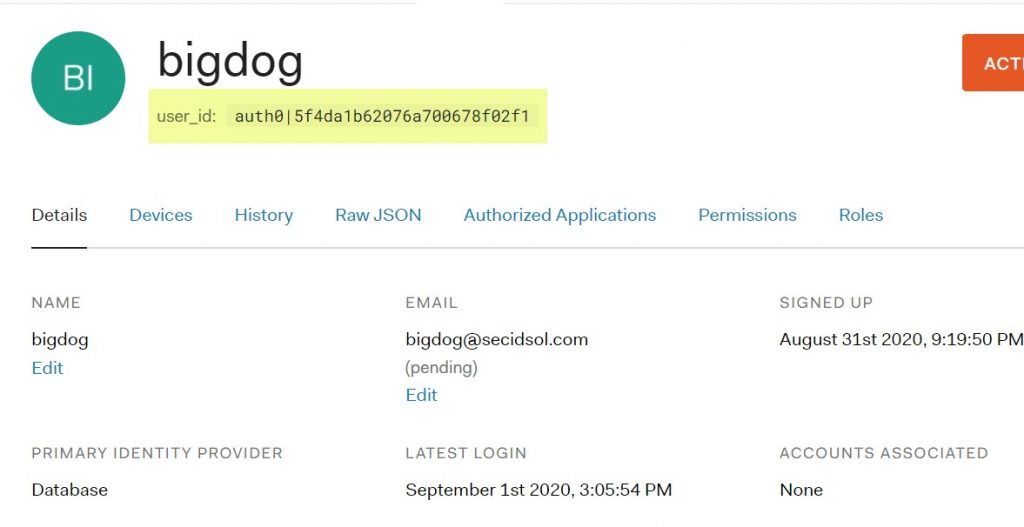
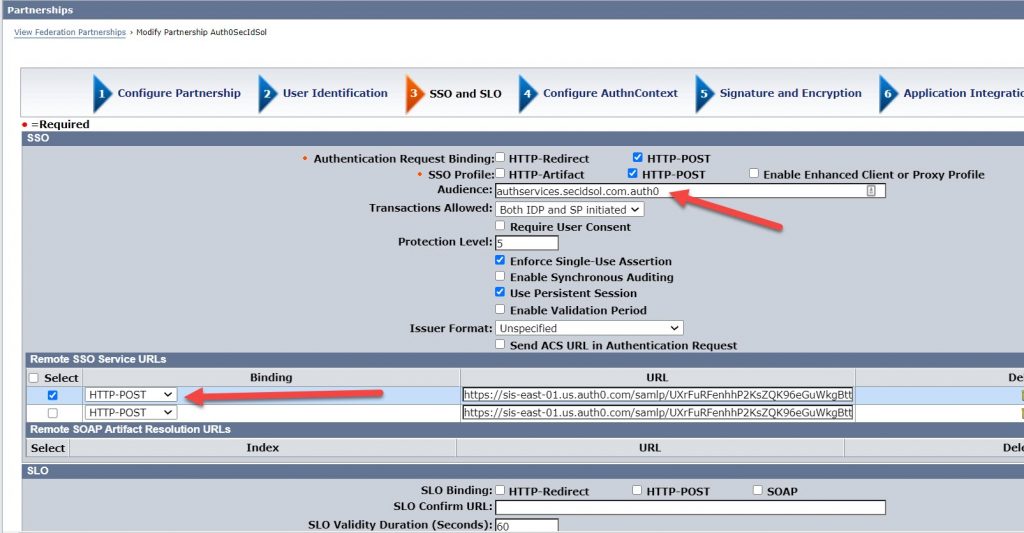
Make sure this value is stored in the userstore or reconfigure the IdP to send a value that is stored in the directory. Enter the audience value and make sure that at least one SSO binding is selected.
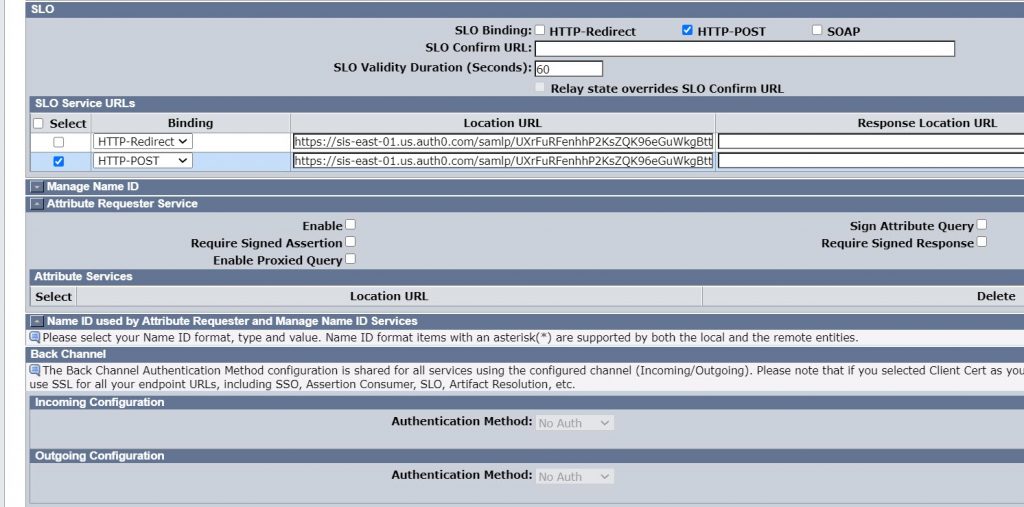
Verify that the correct SLO bindings are selected.
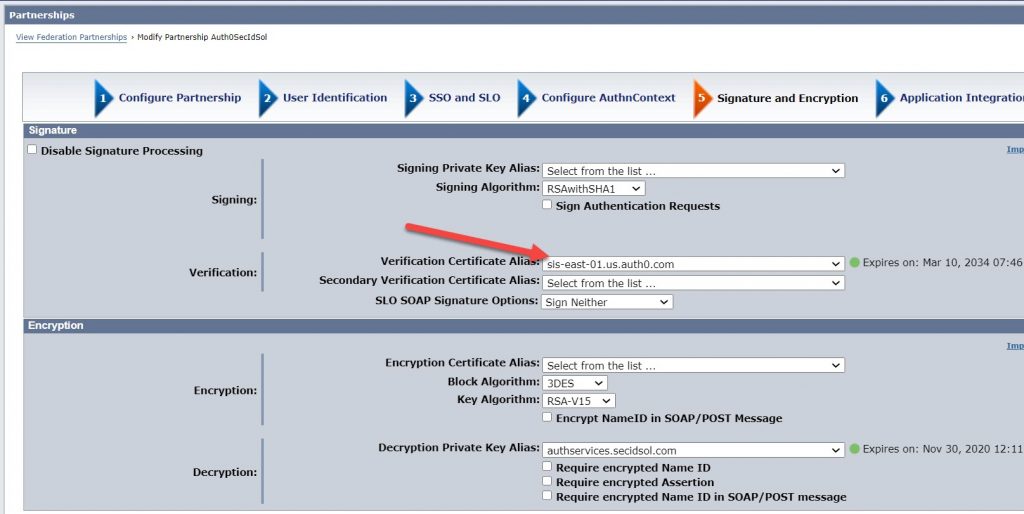
Ensure that the certificate for the IdP is being used as the signature verification certificate.
Enter the URL for the protected application. Select the appropriate redirect method for your application. For this example, we selected HTTP Headers.
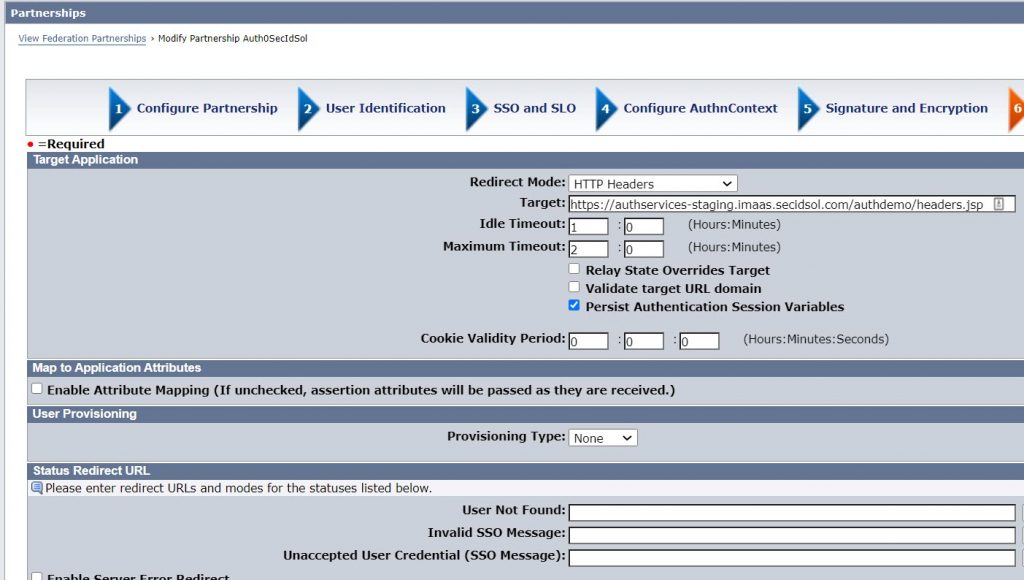
Save the partnership and activate it.
Testing
To test the partnership, copy the Identity Provider Login URL from the Usage tab in the Add-on section for the SAML2 Web App.
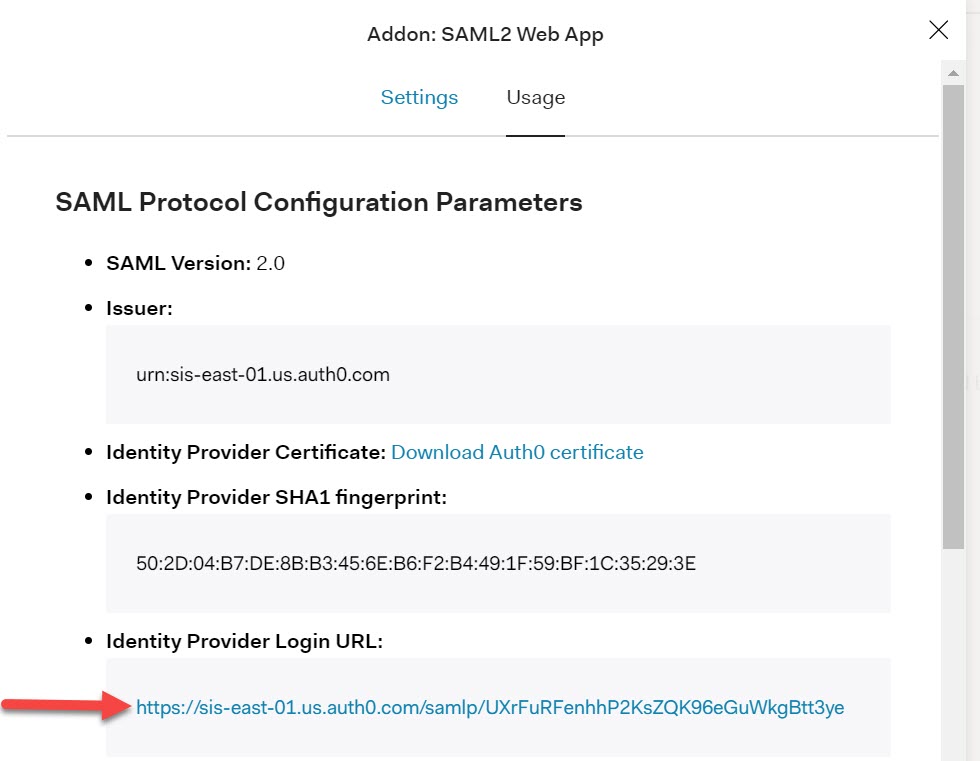
Paste the URL in a browser and you should be prompted by Auth0 for credentials.
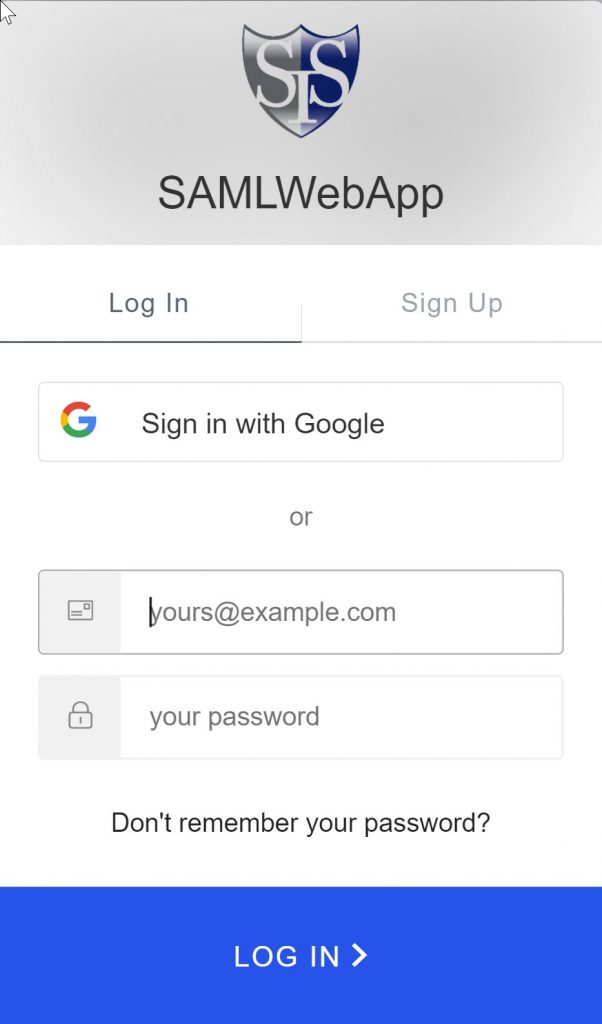
If you have enabled MFA for your application, you will get the following:

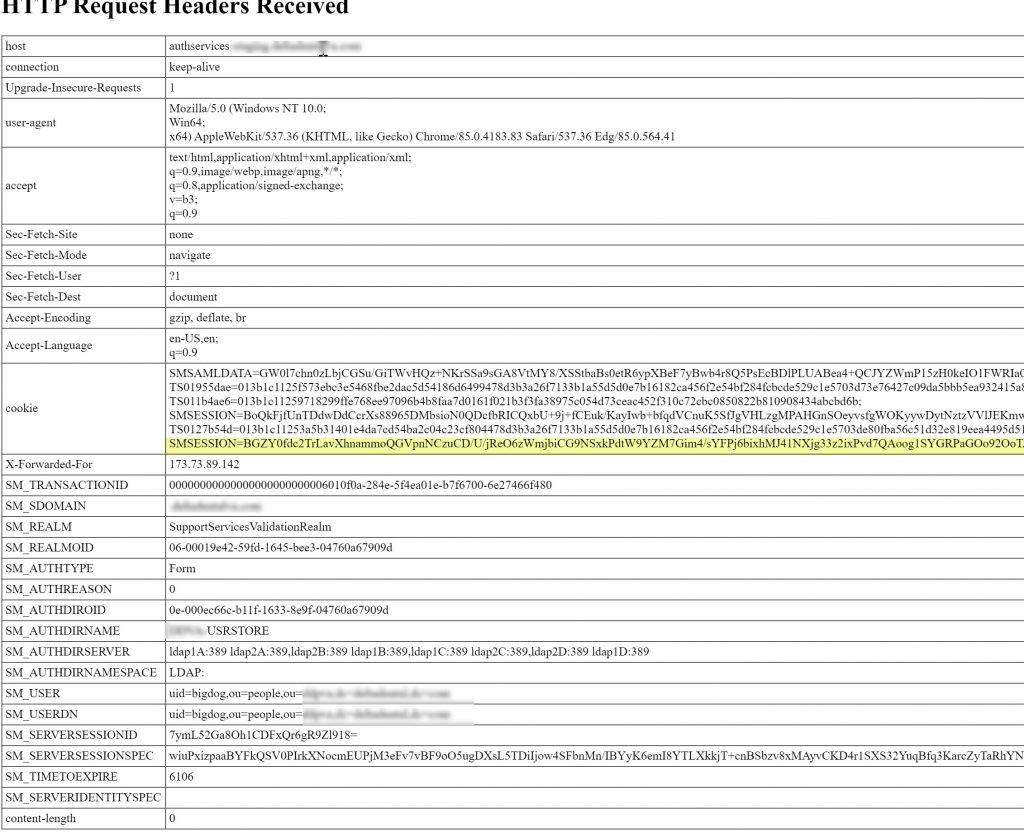
After completing the MFA, you should be redirected to your application. We have a header application for this example. The SMSESSION cookie is highlighted.
Conclusion
Hopefully this example was helpful, but keep in mind that this was a simple example of SAML integration. It’s likely that your solution will need user data mapping to align the user data between the IdP and SP. To that end, user data mapping can be handled within the Settings tab of the SAML2 Web App on Auth0 dashboard. We also recommend using encrypted assertions for any production solution; the details on the required changes can be found here: https://auth0.com/docs/protocols/saml-configuration-options/sign-and-encrypt-saml-requests.
As always, if you need assistance with your SiteMinder or Auth0 solutions, please contact Secure Identity Solutions (SIS).



