As we are regularly asked, “How can we harden our TLS Ciphers for our CA Access Gateway (CAG)?”, this week we will provide a few recommendations to improve your CA Access Gateway’s SSL Cipher score.
How do we see our TLS Cipher score?
Many of our customers use the Qualys SSL Labs Server Test tool (https://www.ssllabs.com/ssltest/) to test the overall health of their SSL implementation. In this post, we will not address all of the test categories, but only the ones directly related to the TLS Ciphers.
The following screenshot shows the results for Cipher Suites that were tested using the Qualys SSL Labs Server Test tool:

There are several issues with the results above:
- TLS 1.0 is insecure and should not be used.
- TLS 1.1 is insecure and should not be used.
- Weak ciphers are being used for TLS 1.2.
Disabling TLS 1.0 / TLS 1.1 on the CA Access Gateway
The CAG’s server.conf is where TLS is managed; that configuration file is located in /CA/secure-proxy/proxy-engine/conf/. Open the server.conf and navigate to the sslparams section. Find the following line:
versions="TLSv1.2,TLSv1.1,TLSv1.0"
Modify the line to only include TLS v1.2, as below:
versions="TLSv1.2"
Restart the CAG server and retest. The configuration section of the test results should resemble the following screen:
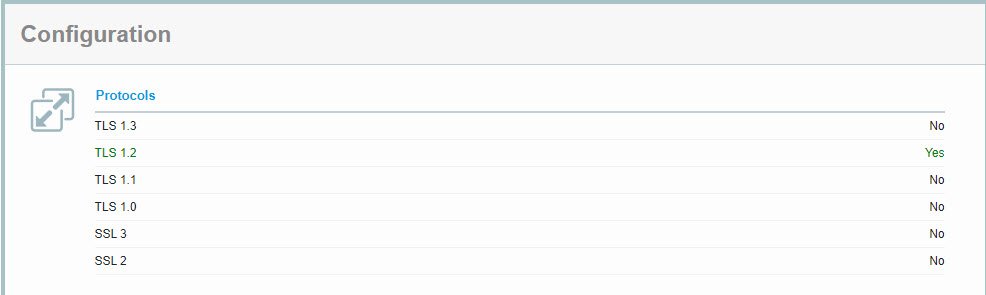
Selecting Strong Ciphers for CA Access Gateway
The CAG leverages OpenSSL as the protocol suite and, as a result, CAG supports all of the ciphers provided by that toolkit. We recommend using the strongest ciphers available, but it is important to keep in mind that some of the hardened ciphers are not supported by older browsers (e.g. IE 8.X) or older devices. The Qualys tool provides a Handshake Simulation tool to assist in the selection of Cipher Suites for the devices and applications CAG must support.
The following is an example of the output of the Handshake Simulation tool:
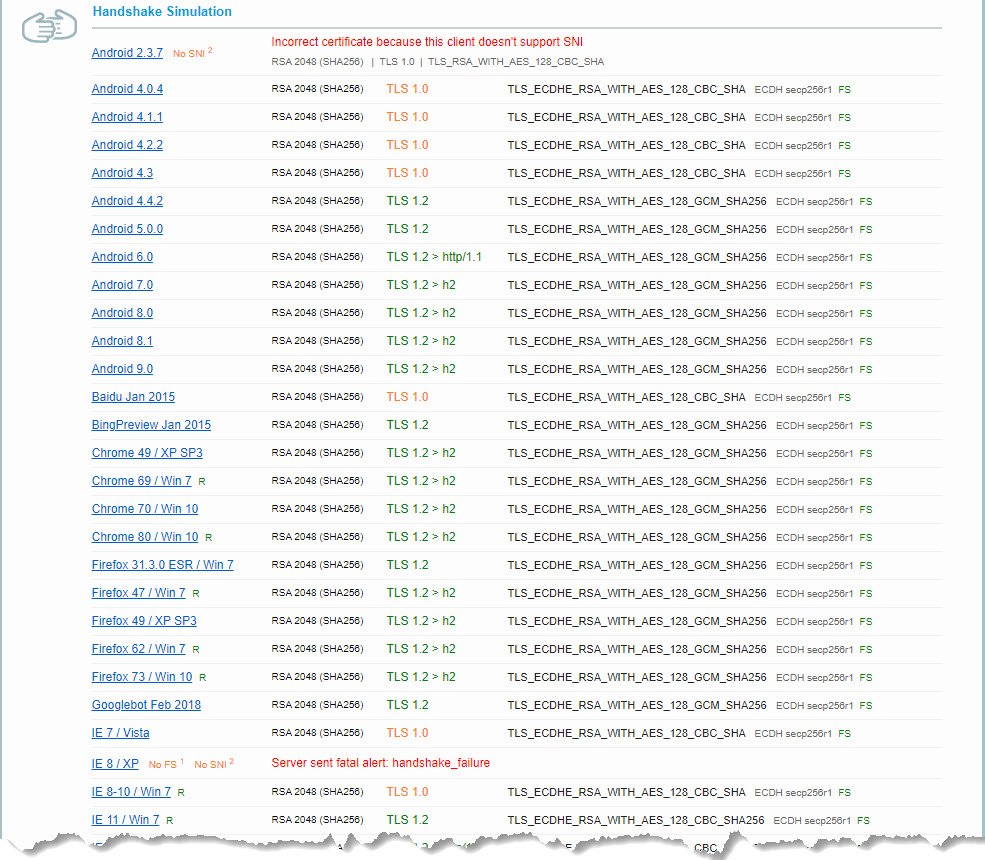
The acceptable ciphers for all of the virtual servers are defined in the sslparams section of the server.conf file, but the virtual server specific ciphers are defined in the httpd-ssl.conf file (which is located in /CA/secure-proxy/httpd/conf/extra/).
It is important to note that the vulnerabilities associated with the cipher suites is always being evaluated by various groups; as a result, a strong cipher today may later be considered weak if an exploit is uncovered. Use tools such as the Qualys SSL Labs tool to regularly assess the strength of the selected ciphers.
OpenSSL provides a comprehensive list of all the supported ciphers, but please keep in mind that some of these ciphers are considered weak and, if implemented, will not improve your SSL Cipher Suite score.
OpenSSL 1.2 Supported Ciphers
https://www.openssl.org/docs/man1.0.2/man1/ciphers.html
For this post we used the following ciphers:
Server.conf
ciphers="+ECDHE-ECDSA-AES256-GCM-SHA384,+ECDHE-RSA-AES256-GCM-SHA384,+ECDHE-ECDSA-CHACHA20-POLY1305,+ECDHE-RSA-CHACHA20-POLY1305,+ECDHE-ECDSA-AES128-GCM-SHA256,+ECDHE-RSA-AES128-GCM-SHA256,+ECDHE-ECDSA-AES256-SHA384,+ECDHE-ECDSA-AES128-SHA256"
httpd-ssl.conf
SSLCipherSuite ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384
After replacing the ciphers, restart the CAG and retest. The following shows the results after the change:
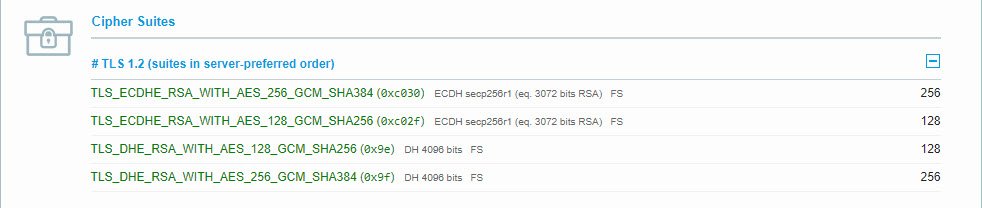
As always, we hope that you have found this information useful. If you need IAM assistance, reach out to SIS today and we would be happy to assist you. And subscribe to our newsletter to be notified about the posting of future articles and other SIS news.

